Internet users risk losing their accounts. The media regularly reminds us of this. In the first three months of 2025 alone, the number of account thefts on Telegram doubled. Attacks also occur on social networks and other websites. Protecting your online accounts is more important than ever. One of the most effective ways to enhance security is by using two-factor authentication (2FA). But what exactly is 2FA, and how does it work? Let’s break it down.
What Is Two-Factor Authentication (2FA)?
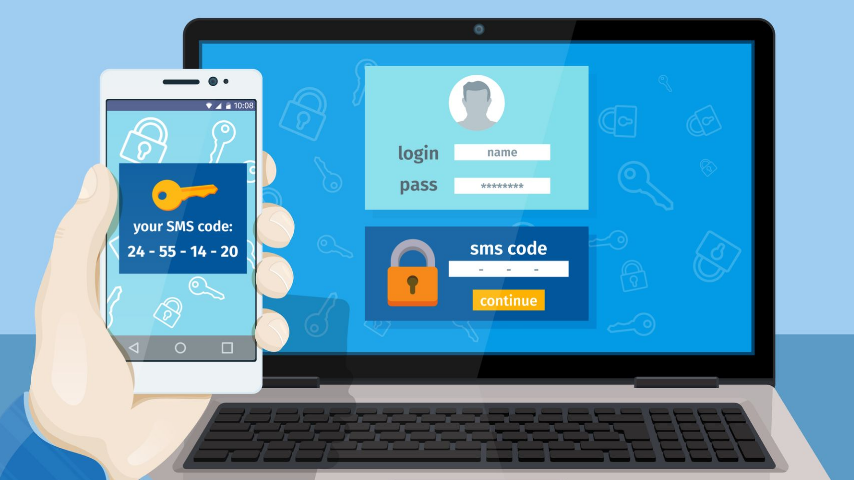
Two-factor authentication is an extra layer of security that requires users to provide two different verification methods before accessing an account. Instead of just entering a password, you also need to confirm your identity through another factor, such as:
- Something you know (e.g., a password or PIN)
- Something you have (e.g., a smartphone, security token, or SMS code)
- Something you are (e.g., a fingerprint or facial recognition)
This approach makes it much harder for hackers to break into your accounts—even if they steal your login and password.
How does 2FA work?
Here’s a typical example of how 2FA protects you:
- You enter your username and password as usual.
- The system then asks for a second verification method, such as:
- A one-time code sent via SMS or generated by an authenticator app (like Google Authenticator or Authy).
- A biometric scan (fingerprint or face ID).
- A physical security key (like YubiKey).
- Only after providing both factors can you access your account.
Common types of 2FA
SMS codes
Users often confirm their identity using a short code that is valid for a limited period of time only. The system generates the code on request and sends it as a text message to either a phone or an email address. You then need to enter the combination of numbers received in a special window on the website.
This method is simple and convenient, which is why it has become so popular. However, it has a major drawback: low reliability. An attacker can intercept an email or text message and log into your account.
Authenticator apps
There is a method similar to the first one, but with its own nuances. It involves using mobile applications for two-factor authentication. Examples: Google Authenticator, Authy, FreeOTP and OTP, Microsoft Authenticator and LastPass Authenticator.
These applications generate codes that are only valid for 30 seconds, which improves security. This method can be used offline. It is simple to use and is free. Such applications can support multiple accounts registered in different systems.
Backup codes
As well as short-term codes, there is a set of codes that are generated in advance. These must be stored in a safe place. Each code can only be used once. Once the backup codes have been used up, you need to request new ones.
This method has its drawbacks. Firstly, users may forget where they stored the backup codes or lose them. Secondly, there is a risk that an attacker may find the record and use it. Thirdly, the user may forget to generate a new set of backup codes when the old ones run out, which will either result in the account being lost forever or needing to be restored.
Biometric verification
You can verify your identity using unique physical or behavioural characteristics. This can include your voice, facial features, fingerprint, vein pattern, iris, as well as your facial expressions, gestures, handwriting or gait.
Such data is difficult to forge. It is impossible to imagine a situation in which another user could impersonate you. However, the use of false biometrics is still possible.
Hardware tokens
These are physical security keys in the form of USB flash drives or NFC cards for various applications, such as accessing remote servers and cloud services. Examples: YubiKey and Google Titan.
Why Is 2FA important?
- Prevents unauthorized access – Even if someone steals your password, they won’t be able to log in without the second factor.
- Protects against phishing – Many scams trick users into revealing passwords, but 2FA adds an extra hurdle.
- Safeguards sensitive data – Essential for banking, email, and work accounts where security is critical.
Attackers most often target accounts that are not protected by two-factor authentication (2FA). A Microsoft study conducted in 2020 found that 99.9% of hacked accounts did not use 2FA. According to Gazeta.ru, fraudsters stole user accounts on various online platforms three times more often in 2024, and two-factor authentication was not used in most cases.
It is becoming increasingly reckless to abandon this method of account protection. As the number of cyberattacks increases, 2FA remains an effective way to protect yourself from third-party fraud online.
2FA is mandatory for websites that store critical data. For example, gaining access to Gosuslugi could allow an attacker to take out a loan using electronic copies of documents. Social media and messenger accounts provide fraudsters with great opportunities to lure money out of users under someone else's name. Anything related to financial management should be protected with two-factor authentication. Prioritize enabling 2FA among other accounts for those used to store multiple passwords.
Using two-factor authentication ensures compliance with regulatory requirements for data monitoring and protection.
-
According to Federal Law No. 152-FZ 'On Personal Data', operators and third parties must ensure the confidentiality of any personal data they have access to. At Cloud4Y, you can rent cloud infrastructure for storing personal data.
-
The GDPR (General Data Protection Regulation) has been a European standard since 2018. It applies to all companies that work with the personal data of EU citizens.
-
The PCI DSS (Payment Card Industry Data Security Standard) comprises requirements developed to protect payment card data. These requirements apply to all companies that work with card data.
The Google case confirms the positive impact of two-factor authentication (2FA) on data security. In October 2021, the company automatically activated two-factor authentication for all accounts. According to Google, this reduced the number of hacks by 50%.
Should you use 2FA?
While no security method is 100% foolproof, enabling 2FA significantly reduces the risk of account breaches. Many major platforms support it—so if you haven’t set it up yet, now’s the time.
Check your account security settings and follow the steps to activate 2FA. Opt for authenticator apps or hardware keys for stronger protection than SMS.
Stay safe and secure your accounts with two-factor authentication — it’s one of the easiest ways to keep hackers out!


