With the development of information technology, online security and privacy are becoming increasingly important. Cybercriminals are constantly improving ways to steal personal data, Internet service providers monitor their customers and limit their capabilities in various ways.
VPN (Virtual Private Network) allows creating a secure encrypted connection on the Internet and prevents intrusion by third parties when exchanging information over the network. The technology primarily was developed for corporate tasks, but later its benefits were acknowledged by ordinary users.
In this article, we explain what you need to know about VPN technology, how it works, and how to implement a VPN connection.
What is a VPN
A VPN is a virtual private network that connects multiple devices by tunneling their traffic over another network connection. In simple words, VPN is a technology that allows you to anonymize and secure your activities on the Internet or any other network.
For a deeper understanding of how the technology is used, let’s take a closer look at the components of the term virtual private network.
Virtual means that the VPN is created by software as a separate layer on top of another network (for example, over the Internet). Transmission is tunneled - the traffic is wrapped in a separate tunnel, which goes through a lower-level communication channel. The information in the VPN tunnel is encrypted to prevent interception of the data from the outside.
Private. A VPN is an internal network with only trusted devices. Although the connection can also be carried out through an external or public network, it is separated from the main communication channel with end-to-end encryption.
Network. The connection is between two devices, a client and a VPN server, thus creating a single network.
How does a VPN work?
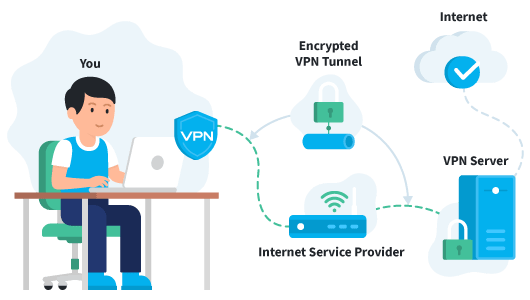
A VPN connection consists of two components: the server - device that hosts the core software, scanning certain ports while waiting for a connection with the client to be established; the user's device, from which the connection to the remote server is established.
- When the user browsers the web, traffic on his computer is encrypted by VPN software and sent to the VPN server through a secure connection.
- The VPN server then decrypts the data from a computer.
- The VPN server sends data to the Internet and receives a response intended for the user.
- The traffic is then encrypted again by the VPN server and sent back to the user.
- The VPN software on the user’s device decrypts the data so that you can understand and use it.
Benefits of a VPN
Hiding browsing activity from Internet Service Provider (ISP). VPN technology protects network traffic from intruders and hides Internet activity from network providers, who often share data with third parties. All that the ISP sees is the fact of connection to the VPN server, the amount of data transmitted, and the duration of the connection.
Sometimes VPN is used to bypass network bans imposed by the administrator or ISP. For example, restricting access to blocked resources or cutting speeds for file sharing sites.
Such possibilities are available thanks to traffic routing via VPN-server. This means that requests sent by the user are first transmitted through a tunnel to the server, and only then sent over the Internet to the desired web resource. This makes surfing the Internet anonymous and allows access to resources that have blocked the IP address of the client.
Protection against hackers. VPN makes it hard or even impossible to intercept information between the client and the server because all traffic is encrypted and inaccessible to those without an encryption key. This is especially useful when transmitting valuable commercial information, as well as in the case of connecting over unsecured public Wi-Fi networks.
Remember, a VPN is not the ultimate solution to cybercrime. Be sure to combine it with a good anti-virus solution to cover all possible problems.
Accessing geo-blocked websites. In some countries, governments severely censor the Internet and block access to certain services and websites. For example, China bans Instagram, Twitter, and Facebook. Foreign states can also restrict access to certain media resources because they consider them a threat to the government. In these countries, such censorship greatly affects the freedom of speech.
A VPN allows users to bypass censorship by enabling them to connect to a server in a different country. Therefore, you can browse the Internet as if you were in another country and access sites and services that are not available locally.
Accessing business network. More and more companies are moving to remote work. Employees are connecting to the Internet via VPN to access the company network from home. This allows them to work securely and efficiently.
Business travelers often use VPNs to access their company’s network, including all of its local network resources on the go.
VPNs provide better overall security, improved performance, remote access, and anonymity. If you need to protect your business online, contact Cloud4Y specialists. They will study the structure of your company, find the weakest points, and develop instructions on how to ensure protection.



