A firewall is a tool for protecting a network from intruders. It works as a filter, constantly scanning data coming into your network and preventing suspicious data from getting through. In this article, we will take an in-depth look at the types of firewalls and their work.
How firewalls work
Simply put, a firewall is like a vigilant security guard who knows millions of potential criminals by sight. He inspects all the people entering the building and once he finds someone suspicious among them, he will not let them in. Similarly, a firewall works by monitoring and regulating the traffic coming into and out of your network. This is accomplished through a variety of methods, including packet filtering, proxy service, and stateful inspection. In addition, the firewall prevents intruders from using your system to spread malicious code.
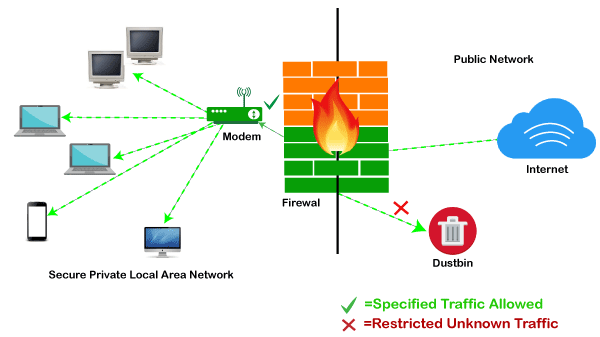
Firewall capabilities
-
Protection against spoofing. If your computer is exchanging data with another computer and the IP addresses of both devices are known. Scammers can spoof their traffic to look like it is coming from one of the legitimate computers, but send it from a different IP. The firewall will spot spoofing and prevent fake traffic from entering your network.
-
DDoS attack protection. If attackers send multiple requests to your device from an infected device trying to disable your resources, the firewall can detect and filter it out.
-
Blocking data transmission to an unidentified IP address. If you have downloaded and installed malware on your computer, it may try to transfer your data to an intruder. The firewall can automatically stop this process.
Methods for computer protection
Batch filtering. The data is organized into packets. While the firewall performs filtering, it checks the data packets by comparing them to filters containing information about malicious data. If the data packet matches the threat parameters, it is blocked and safe packets are passed on.
Proxy service. In this case, the firewall acts as an intermediary between the computer and all devices attempting to connect to it. It prevents intruders from connecting directly to your computer.
Status monitoring. The firewall checks each data packet and compares it to the threat database. During the inspection, the firewall checks, where the data is coming from, what ports it uses, and what applications it is related to. If the data packet passes the check, access is permitted. Otherwise, it cannot pass through.
Types of firewalls
Hardware firewalls
Work independently of the computer being protected and filter information coming from the Internet into the system. If you have an Internet router, it most likely has a firewall.
The hardware firewall checks data coming from the Internet and determines if it is safe. It checks each data packet and finds out where it came from and where it is located. The data collected by the firewall about each packet is then compared to a list of permissions to determine if it matches the profile of the data to be rejected. Cisco or Zyxel firewall can protect all computers connected to it, making it an easily scalable solution.
Software firewalls
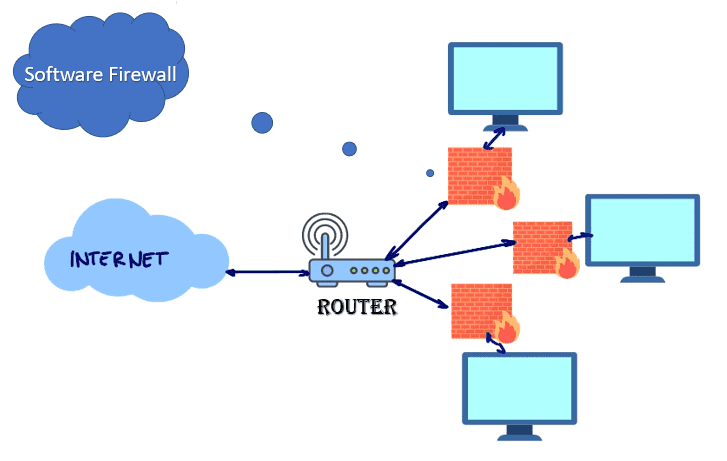
Such firewall is installed directly on the computer. The user configures it according to his needs. A software firewall filters incoming and outgoing data, checks for maliciousness, as well as monitors traffic trying to leave your computer, preventing it from being used to attack other networks or devices. Software firewall must be installed on every computer on a network.
How does the firewall protect information?
A firewall prevents the following security threats:
-
Backdoors. Some applications that permit remote access to the computer may contain bugs allowing attackers to get into the system as if through a backdoor. The same loophole bugs can be found in the operating system itself.
-
Denial of service. A cyberattack can cause a server to crash. A connection request is sent to the computer, but the server cannot find the recipient. Due to the overflow of one-sided requests, server operation is severely slowed down.
-
Macros. These special scripts allow the launching of a series of complex processes with a single executable rule. By accessing applications on the computer, an attacker can run their malicious macros there. This can lead to data loss or system malfunction.
-
Remote access to the system. Unauthorized users can access your computer and perform various actions on it. If it is a hacker, they can access your confidential data, and run unwanted software, etc.
-
Spam. It is not dangerous on its own, but it often contains links to malicious resources. Clicking these links may threaten your system.
-
Viruses. These self-replicating programs spread among devices over the Internet. Viruses can cause significant damage, from stealing data to gaining access to your computer.
A properly configured firewall will protect against most cyber threats, but not all. Therefore, we recommend combining these with other means of protection.



