A Virtual Private Network (VPN) is a technology that allows users to connect to the internet securely through an encrypted connection. By routing traffic through this private tunnel, a VPN helps safeguard personal data and enables secure access to corporate or home networks.
How Does a VPN Work—and Why Is It Important?
Every internet-connected device has a unique IP address, which serves as a digital identifier. Websites and online services can use this address to track a user’s location, browsing activity, and transmitted data potentially compromising privacy.
A VPN solves this problem by establishing an encrypted tunnel between the user’s device and a remote server. Once activated, all internet traffic passes through this secure tunnel to the VPN server, which then replaces the user’s real IP address with its own.
One of the key advantages of a VPN is end-to-end encryption, which ensures data protection even on unsecured networks—such as public Wi-Fi in cafes, airports, or hotels. Without a VPN, these networks are vulnerable to attacks like traffic interception and DNS spoofing, putting sensitive information (passwords, banking details, private messages, and browsing history) at risk. A VPN acts as a shield, preventing hackers from accessing your data while maintaining online privacy.
For businesses, VPNs have become a critical component of secure remote work. Employees can safely access company networks, cloud services, and SaaS applications from anywhere without exposing sensitive data to potential breaches. Many corporate tools, including virtual desktops and remote collaboration platforms, rely on VPN technology to ensure encrypted connections.
How a VPN Connection Works: A Step-by-Step Breakdown
When a user connects to a Virtual Private Network, their device establishes a secure, encrypted link to a remote VPN server. This process involves multiple layers of protection to safeguard data and preserve privacy. Here’s how it works:
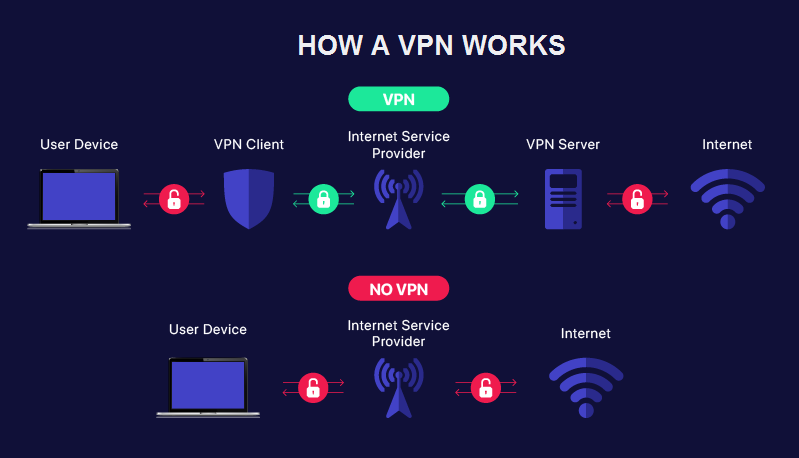
1. Establishing a Secure Connection
The user’s device authenticates with the VPN server using secure protocols such as *OpenVPN, WireGuard, IKEv2/IPsec*, or *L2TP/IPsec*. During this step:
-
The VPN verifies the user’s identity (via login credentials, certificates, or cryptographic keys).
-
The two parties negotiate encryption settings.
2. Creating an Encrypted Tunnel
Once authenticated, the VPN sets up a secure tunnel between the user’s device and the server. All data passing through this tunnel is encrypted using robust algorithms like *AES-256* or ChaCha20, making it unreadable to outsiders—even if intercepted.
3. Routing Traffic Through the VPN Tunnel
All network activity—including web browsing, DNS queries, and VoIP calls—is routed through the encrypted tunnel. At this point:
-
The user’s ISP or local network administrator can only see an encrypted data stream.
-
They cannot decipher the contents, final destination, or specific services being accessed.
4. IP Masking & Internet Access via the VPN Server
The VPN server acts as an intermediary, forwarding requests to the internet on the user’s behalf. Key effects:
-
The user’s real IP address is replaced with the VPN server’s IP.
-
To external websites and services, the traffic appears to originate from the VPN server’s location, hiding the user’s true geo-location and identity.
5. Secure Data Transmission via Encrypted Channel
When the target server (e.g., a website or cloud service) responds, its data is first sent to the VPN server, which performs a critical security step:
-
The VPN server re-encrypts the data before sending it back through the secure tunnel to the user’s device.
-
Only the user’s device possesses the correct decryption key, ensuring that even if intercepted, the data remains unreadable to third parties.
Technical security measures:
-
Encryption: The data is converted into an unreadable form using cryptographic algorithms. Without the matching key, intercepted data cannot be decrypted.
-
Encapsulation: Each packet is wrapped in an additional security layer, concealing its original content and destination.
-
Protection against MITM (Man-in-the-Middle) attacks: Even if an attacker attempts to intercept the traffic (e.g., on a public Wi-Fi network), all they see is an encrypted stream that requires cryptographic keys for decryption.
Thus, a VPN not only changes the IP address but also creates a fully encrypted communication channel. This technology is essential when working with sensitive data, using public networks, or accessing company resources.
Types of VPN Connections
VPN technologies vary in architecture, purpose, and methods of establishing secure connections. Different connection schemes are used depending on the task, each with its own characteristics.
Remote Access VPN
This type of connection is designed for individual users who require secure access to corporate networks or personal resources from anywhere in the world. The principle involves establishing a secure connection between the user’s device and a VPN server. The user launches a VPN client on their device, and after authentication, an encrypted tunnel is created through which all traffic is routed. This allows users to access internal company resources as if they were on the local network. This type of VPN is widely used by remote employees to connect to corporate systems, as well as by private users to protect their data on public Wi-Fi networks.
Site-to-Site VPN
This technology is used to connect entire local networks over the internet. A Site-to-Site VPN creates a virtual private network between offices, data centers, or cloud services. A VPN gateway is deployed at the edge of each network, automatically encrypting and transmitting traffic between networks without requiring manual connection from users. Such solutions often use IPsec or OpenVPN protocols and are commonly employed by corporations with distributed branches, hybrid cloud infrastructures, and other scenarios requiring secure data exchange between remote sites.
Point-to-Multipoint VPN Topology
This variation of Site-to-Site VPN uses an architecture where one central node is connected to multiple remote nodes. All endpoints communicate through a central hub, which manages connections and security policies. This scheme is particularly common in software-defined networks (SD-WAN) and allows new nodes to be added dynamically without changing the core configuration. Typical applications include banking networks, retail chains with in-store terminals, and remote monitoring systems for IoT devices.
Double VPN / Multihop VPN
An advanced security scheme where traffic passes sequentially through two or more VPN servers before reaching the internet. Each server in the chain adds a new layer of encryption and changes the IP address, significantly enhancing anonymity and complicating traffic analysis through temporal correlation. However, this architecture increases connection latency due to the need to pass through multiple nodes. Such solutions are in demand among journalists and activists in countries with strict internet censorship, cybersecurity professionals, and users for whom maximum confidentiality when handling sensitive data is critical.
VPN Application vs. VPN Network: What’s the Difference?
From an IT infrastructure perspective, a VPN application and a VPN network are two interconnected yet fundamentally different components of virtual private network technology.
A VPN application is client software installed on an end-user device (computer, smartphone, or tablet). It serves as an interface between the user and the VPN infrastructure, significantly simplifying the connection process. The application automatically configures connection parameters, including server selection, encryption protocol, and authentication. The user only needs to launch the program and click the connect button—all technical details (key exchange, tunnel establishment, traffic routing) are hidden under the hood. Modern VPN clients often include additional features such as a Kill Switch, DNS leak protection, and specialized server selection (e.g., for streaming or torrents).
A VPN network is the underlying infrastructure that powers the virtual private network. It includes physical or cloud servers, communication channels between them, routing software, and a user authentication system. Unlike the application, a VPN network can operate completely autonomously—its configuration is handled at the operating system level (via built-in VPN clients in Windows/macOS/Linux) or network equipment (routers, firewalls). Corporate solutions often use this approach, deploying VPN gateways for secure connections between branches or remote employees without the need to install separate applications on each device.
The key differences lie in the fact that a VPN application is focused on end-user convenience, abstracting away technical details, while a VPN network is a fundamental technology that can be implemented in various ways. An application always requires pre-installation, whereas a VPN connection can be manually configured through system settings or network equipment.
In corporate environments, these concepts often overlap: a company may deploy its own VPN network but provide employees with a client application for easy access. Thus, a VPN application is just one way to interact with a VPN network, which remains the core of the entire secure connection system.
Conclusion
In summary, a VPN is a digital security tool that creates a secure tunnel for internet traffic, providing end-to-end encryption for transmitted data. As a result, VPNs reliably protect personal and corporate information from interception on public networks, block tracking by internet providers and advertising systems, and ensure secure remote access to companies' internal resources.




