Information security (IS) refers to the measures taken to protect computer systems, programs, and data from unauthorized access, use, disclosure, disruption, modification, or destruction. In today's world, where technology is ubiquitous, safeguarding digital assets has become a crucial task. IS encompasses a broad range of software, hardware, and other solutions designed to mitigate cyber threats. This article will explore the significance of IS, its necessity, and the threats it faces.
The Importance of Information Security for Businesses
Information security is a field that aims to protect information from various threats and risks. It includes technical, organizational, and legal measures to prevent unauthorized access, data leaks, virus attacks, and other potentially dangerous events.
IS is essential for both large corporations and ordinary users. Research conducted in 2023 shows that cyberattacks worldwide have increased by 25% year-on-year, highlighting the importance of protecting digital assets.
It is important for businesses to prioritize information security as it safeguards data privacy, prevents cyber threats and virus infections, ensures compliance with legislation, preserves reputation, maintains business continuity, protects financial resources and can provide a competitive advantage.
Why do We Need Information Security?
Information security is necessary to protect systems from a variety of threats, including hacking, DDoS attacks that can cause a service or application to become unavailable, data leaks, and other types of attacks. It is important to note that there are many attackers out there, and no one wants their service to become unavailable or their data to be accessible to unauthorized individuals.
There are two distinct types of threats to an organization's security: insider threats and external threats.
-
Insider threats, which can include accidental data leaks or data corruption, originate from within the organization. An employee bribed by an intruder can steal commercially sensitive data. In addition, such threats can arise from trivial mistakes that lead to public access to confidential data.
-
External threats, such as cyber attacks or physical breaches, come from outside the organization. The network may face external threats such as hacking attempts through vulnerabilities, DDoS attacks, and other methods employed by attackers to steal or damage information.
Other reasons why information security is important to a business include compliance with national regulations and maintaining customer trust. Companies are responsible for protecting user data and can do so by implementing security measures. This helps prevent leaks, protects the company's reputation, and avoids legal problems. Without information security services, there is a risk of unauthorized access to confidential information, which can cause damage to the company, its systems, and its clients. Implementing software protection and other security measures can establish the company as reliable and customer-oriented.
The WannaCry attack in 2017 highlighted the significance of information security services. This ransomware blocked data access and demanded a ransom in bitcoins.
Companies that invested in IS tools were largely protected from the attack.
Information Security of Critical Infrastructures
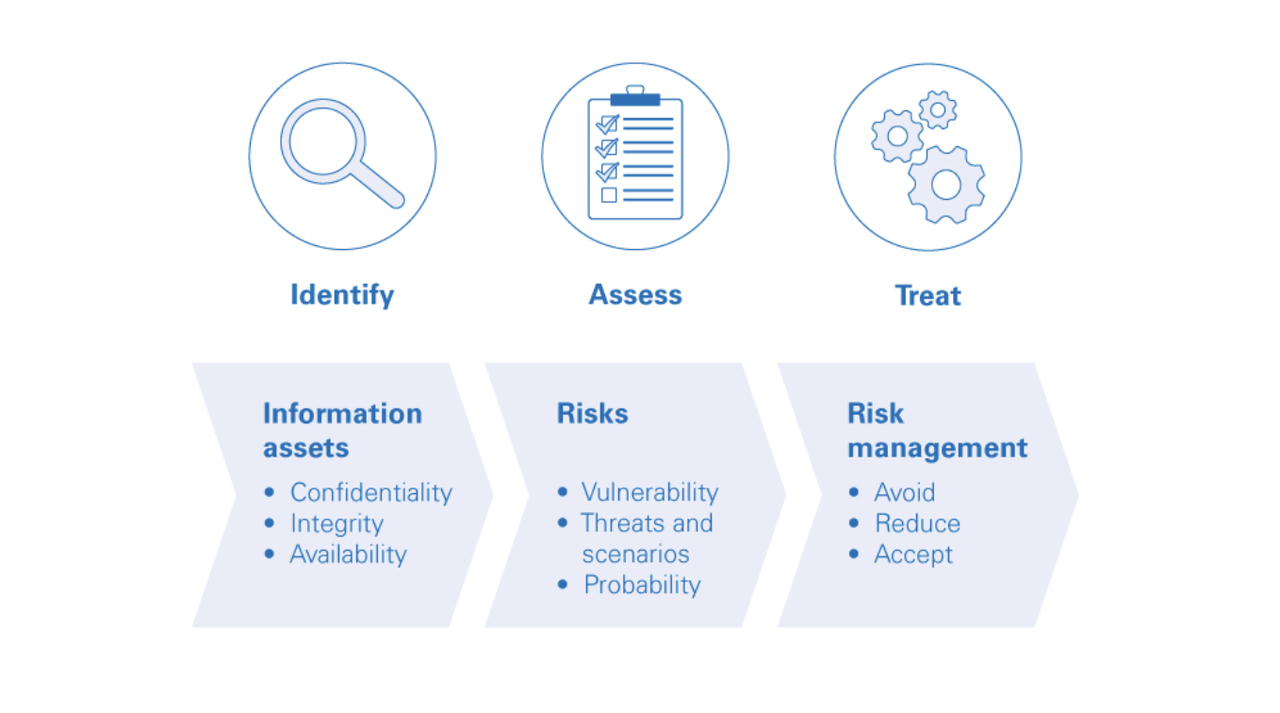
Ensuring the security of key systems and facilities is crucial for the normal functioning of society and the economy.
Information security is vital in achieving this goal, which includes critical infrastructure industries like energy, transport, healthcare, finance, and water.
As part of critical infrastructure protection, information security services deal with
Cyber defence
- Measures to prevent, detect, and respond to cyber attacks on critical infrastructure management and control systems.
- Developing and implementing security measures such as firewalls, intrusion detection systems, and cryptography to protect critical data.
Physical security
- Protecting access to critical infrastructure, such as power plants, water systems, and transportation systems.
- Developing video surveillance systems, motion sensors, and other technologies to monitor and respond to undesirable events.
Risk management
- Vulnerability and threat analysis of critical infrastructure to develop strategies for risk management and mitigation.
- Regular updating of business contingency and disaster recovery plans following cyber-attacks or other incidents.
Implementing and developing standards and regulations
- Compliance with existing information security standards and regulations for critical infrastructure.
- Implementation of international and industry standards to ensure a consistent and high level of protection.
Staff training and awareness
- Information security training for personnel responsible for the management and maintenance of critical infrastructure.
- Regular training to respond effectively to changing threats.
Ensuring the security of IT infrastructure is crucial. It prevents consequences such as downtime, threats to the health and safety of citizens, and the resilience and sustainability of society as a whole.
Key Components of Information Security
To combat cyber threats, it is necessary to implement proactive measures and utilize advanced technologies. An example is a machine learning system that can identify anomalies in user behavior and promptly warn of attacks.
What information security components should an IS service control?
Privacy. It is important to ensure that information is only available to those who are authorized to use it. Access rights and group policies are configured for this purpose.
Data integrity. It is critical to ensure that internal users and external partners are assured that data remains unchanged throughout its lifecycle. No unauthorized changes, no substitution of pieces of information.
Accessibility. Information needs to be protected, yet available when it is needed. Preferably without delay.
Authentication and authorization. IS services are responsible for the implementation and proper operation of user authentication and authorization systems.
As technology advances, information security is also evolving. Using blockchain to provide source code transparency, analyzing big data to detect anomalies, and training neural networks to identify new threats are just a few of the areas of development.
Information Security Tools
There are many tools and the choice depends on your specific needs and level of security. Here are a few of the main categories of tools:
Antivirus software. Programs designed to detect, block, and remove malware such as viruses, Trojans, and spyware. Kaspersky, Dr.Web, McAfee.
Firewalls. Devices or programs that filter and control network traffic to prevent unauthorized access to networks and systems. Cisco ASA, pfSense, WAF.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). Monitor network traffic to identify suspicious activity and take action to block or prevent intrusions. Snort (IDS), Suricata (IDS/IPS), Cisco Firepower (IPS).
Encryption tools. Use encryption to protect data at rest and in transit, ensuring confidentiality and integrity. BitLocker, VeraCrypt, OpenSSL.
Access control systems. Manage user access rights to resources and information to prevent unauthorized access. Active Directory, LDAP, Identity and Access Management (IAM) solutions.
Auditing and monitoring tools. Tools for tracking and auditing user activity and monitoring changes to systems and networks. Splunk, Nagios, Wireshark.
Web filtering and content control systems. Used to filter web traffic, block malicious sites, and control access to specific categories of web resources. Cisco Umbrella, WebTitan, Blue Coat.
Backup and recovery tools. Tools for regularly backing up and restoring data in the event of loss or damage. Veeam, Acronis, Backup Exec.
Vulnerability management systems. Tools for identifying, analyzing and remediating vulnerabilities in network devices and software. Nessus, Qualys, OpenVAS.
These tools are often used in combination to create comprehensive information security strategies in organizations.
Informationsecurity is therefore an integral part of the modern IT world, ensuring the
safety of data and the reliable operation of systems.



