Security tools have always evolved alongside the emergence of new attacks. This is also true in the field of information security. New solutions use firewalls, intrusion detection systems, web filters, anti-virus software streaming, and VPN connection support.
Firewalls check network connections – address/port of destination and sender, routing protocols, session state. But they cannot detect malicious and attacking traffic if it meets the rights and access policies set by the administrator. If an exploit exploits a vulnerability when access is allowed, the firewall will fail to defend against the attack. New solutions are being implemented to improve system security, such as IDS and IPS.
Differences between IDS and IPS
IDS is an intrusion detection system and IPS is an intrusion prevention system. They are so similar that are usually referred together. Previously IDS was a separate tool, but later it became part of IPS. When compared to traditional information security solutions, IDS/IPS can provide a higher level of network protection.
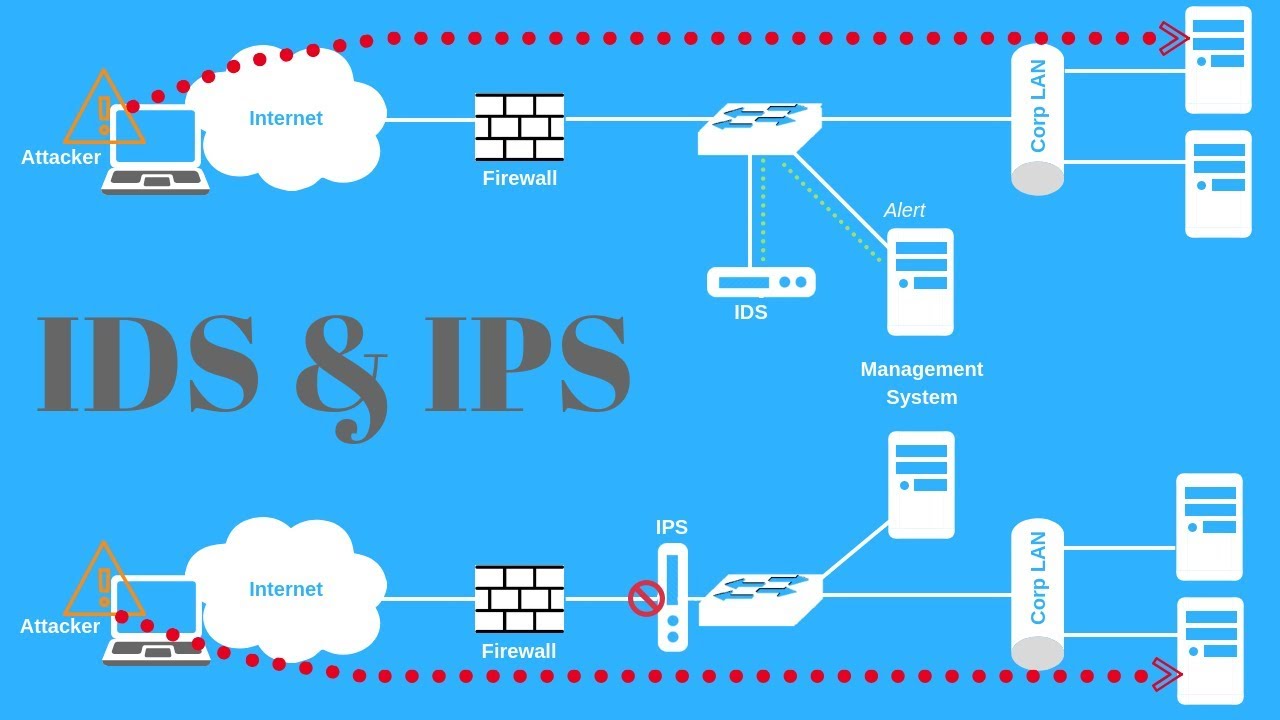
The main difference is in the way they respond to incidents. An IDS is a monitoring tool. It detects potentially dangerous activity and alerts users. IPS is able not only to detect the problem but also to take action to deal with the threat, for example, to break the connection or block the IP address where suspicious activity is coming from.
There is also a difference in the way the infrastructure is integrated and interacts with the network traffic. IDS is installed in parallel to the network flows, and this system handles a copy of the passing traffic. IPS is incorporated into the network, allowing traffic to pass through itself. In this situation, IDS is preferable, because when the limits allocated to the protection solution to handle traffic are exhausted, IDS will not impact network activity. And IPS can become a bottleneck in the protection system, overloading the firewall hardware
What intrusion detection and prevention systems allow you to monitor? As mentioned above, IDS monitors traffic. It compares network activity with its own database of network threats. With this approach, the solution is trained to detect:
- Network attacks;
- Data access attempts;
- Malware activity;
- Port scanning attempts;
- Abnormal activity;
- Use of botnets and mining pools;
- Violations of security policies
Types and Technology of IDS/IPS Systems
IDS systems are divided into two categories: by the site of installation and by operation principle. Let's consider both.
By installation site
-
Network Intrusion Detection System (NIDS). Once installed, the system begins to analyze the traffic of all network devices, inspecting every packet from the data link layer to the application layer. Network Intrusion Detection Systems detect not only external but also internal threats. The higher the traffic volume, the higher the demands on the CPU and RAM. A large amount of data can slow down NIDS or even cause it to bypass individual packets, causing risks.
-
Host-based Intrusion Detection System (HIDS). They are installed on one host inside the network and analyze and protect only its traffic. The principle is simple: HIDS takes a snapshot of the current version of the host and compares it with the previous one, detecting possible threats. It is recommended for mission-critical hosts with little or no configuration changes.
-
Perimeter Intrusion Detection Systems (PIDS). A simpler solution compared to the previous ones. It does not protect the entire network but only alerts if the network is breached. Just like a fence around a house.
-
Virtual Machine-based Intrusion Detection Systems (VMIDS). The solution is based on virtualization technologies and eliminates the need to deploy the detection system on a separate device. All you have to do is deploy VMIDS on a virtual machine to detect suspicious activity.
-
Application Protocol-based Intrusion Detection System (APIDS). The system provides control of packets that are transmitted over an application layer protocol. For example, those used to access the SQL database.
-
Hybrid Intrusion Detection System (HyIDS). This is a hybrid solution combining the features of the above ones.
According to the operation principle
-
Signature. The principle of operation is similar to that of antivirus software. Such IDS analyze signatures with those available in a constantly updated database. If there is no access to the database or it is outdated, the signature solution is less effective. There is also a risk that a new attack with an unknown signature will not be detected correctly. Signature-based IDSs track system state, not events.
-
Anomaly-based. The solution relies on machine learning technologies. To work correctly in a facility requires pre-training. The training period depends on the complexity of a company's IT infrastructure. The working principle is as follows: the system studies the network operation for the current time and compares it to a similar period in search of anomalies of three types - statistical, protocol, and traffic anomalies. Such protection systems are effective but complicated.
Popular IDS/IPS solutions
Zeek

A network-based intrusion detection system based on a Unix system. Features a proprietary language for writing policies that will determine the sequence of actions when an attack is detected or alarm sensors are triggered.
Snort

A cross-platform open-source IDS/IPS solution. It is capable of logging, analyzing, and searching by content. Used for active blocking or passive detection of a wide range of attacks and probes.
Security Onion
It is more than just an IDS/IPS, rather an entire Linux distribution designed to monitor network security and prevent unauthorized network intrusions. It contains many useful tools and combines signature-based and anomaly-based security tools.
Suricata

An open-source solution that uses relevant technologies to increase speed. Suricata integrates with standard applications and supports most of the available modules. It works according to the signature analysis principle.
Corporate cloud provider Cloud4Y offers a secure cloud infrastructure that complies with FSS and FSTEC requirements. In addition, customers can use additional security solutions or perform an IS audit of their infrastructure. For more information, please contact our managers: sales@cloud4y.ru or call 8 (495) 268 04 12.




